Meltdown and Spectre: Why the Commotion?
9 min read
Another commotion is spreading across the Internet about a potential threat: Meltdown and Spectre critical vulnerabilities found in Intel and other ARM CPUs will be exploited and hackers will steal your money, erase your data and mow your cat, blah blah blah.
If hackers knew or could have exploited it, you would have noticed. Catching fire now is too late. “Spectre” vulnerability is 15 years old. Now, please remember the Year 2000 bug hoax and follow the money ????
I’d like to be the bearer of good news, because you are all wrong about this threat. NO NEED TO PANIC and here is why:
These Threats Have Re-Gained Attention One Year Ago

Google researchers from Project Zero team at Google re-discovered vulnerabilities in semiconductors in June 2017 and reported them to chip makers Intel and AMD, as well as Arm Holdings, the chip design company.
Before the issues described here were publicly disclosed, Daniel Gruss, Moritz Lipp, Yuval Yarom, Paul Kocher, Daniel Genkin, Michael Schwarz, Mike Hamburg, Stefan Mangard, Thomas Prescher and Werner Haas also reported them; their writeups/blogposts/paper drafts are at:
Curiously, only today these threatening news are reaching a spike on the social medias, following the Google Project Zero’s first post from January 3rd, 2018. Reason is, they agreed to a coordinated disclosure date of January 9, 2018:
We are posting before an originally coordinated disclosure date of January 9, 2018 because of existing public reports and growing speculation in the press and security research community about the issue, which raises the risk of exploitation.
Every blogger about security go with their traditional warnings and “overview”, spreading stressful and useless re-shared information over the social medias. LinkedIn is especially targeted because it’s a professional networking social media, where everyone wants to be recognized and taken seriously, in the hope to get a better status maybe.
It’s been a year since its re-discovery and the industry is on the spot since 2003. Why is everyone catching fire now?
[callout type="info" size="lg"]
But Who is Project Zero?

Project Zero is Google’s new crack-squad of hackers (or “security researchers” as Google describes them) who have been hired to find and fix bugs on the internet.
The team includes George Hotz aka geohot, author of the blackra1n jailbreak for iPhone iOS 3.1-3.1.2 (I personally remember it as I am old enough to have used it on my 3Gs in 2009 ????)
[/callout]
Intel CEO Sold Half Of His Stock Before Security Flaws Became Public

This one only should raise concerns, as Intel CEO Brian Krzanich sold half of his stock several months after learning there were security flaws in billions of microchips across the industry. What about the timing of the sale and his confidence in the company?
On Nov. 29, Brian Krzanich, CEO of Intel, reported several transactions in Intel stock in a Form 4 filing with the SEC. Krzanich sold shares 21 times during 2017, according to filing with the Securities and Exchange Commission. This report by the Motley Fool means that he sold the most stock as allowed under corporate by laws, to now hold only the minimum number of shares he’s required to own.
Last month. Before the security flaws became public. Obviously this is a lot of money ????
It’s also interesting to compare Intel vs AMD stocks for this first week: Intel goes down on January 4th, while AMD goes up:
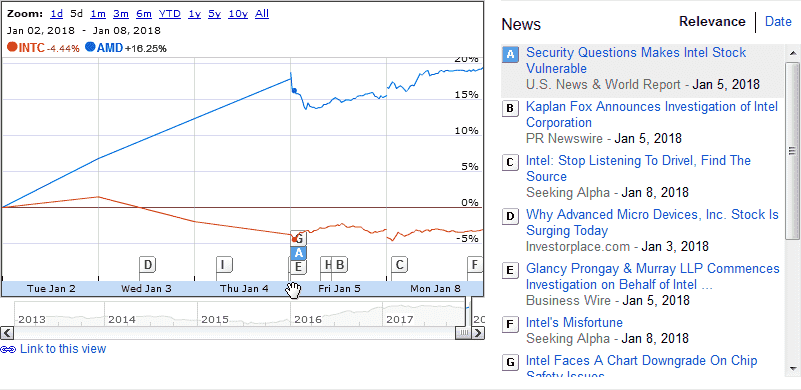
Seems like AMD users do not care too much about his flaw ????
Potential Exploits Are Actually “Proof of Concept”, “difficult and limited”
By Google researchers’ own words again:
During the course of our research, we developed the following proofs of concept (PoCs): blah blah
Explanation: these guys are paid by Google to do some research on potential vulnerabilities that may lurk around, waiting to be found and exploited. Then they “ethically” try to exploit them, then they release papers about it and hope that the industry will follow and release patches before disclosure. Finally, they decide of a press release date, which was set on January 9th, 2018.
According to the creators of this commotion, exploiting these vulnerabilities is “difficult and limited” on the majority of Android devices. It’s not just any JavaScript kiddies that can implement that and spread it like a worm. You actually need some serious skills in CPU architecture and framework development to be able to grasp the complexity of the concepts described here.
Patches Have Been Released, Many Other On Their Way
- Microsoft: IE and Edge
- Google Chrome 64+
- Every Google and Android products
- Mozilla Firefox 57+
- Apple: WebKit’ Safari 10.0.2
- Apple: iOS 11.2, macOS 10.13.2, and tvOS 11.2
- Intel, Linux, nVidia, cloud providers, SGX, etc
- etc
Another friendly tech savvy going by the handle of Hannob even created a Github page to summarise ALL the patch status for Meltdown / Spectre available around. Not less than 24 contributors participated, and all of them started on December 31, 2017.
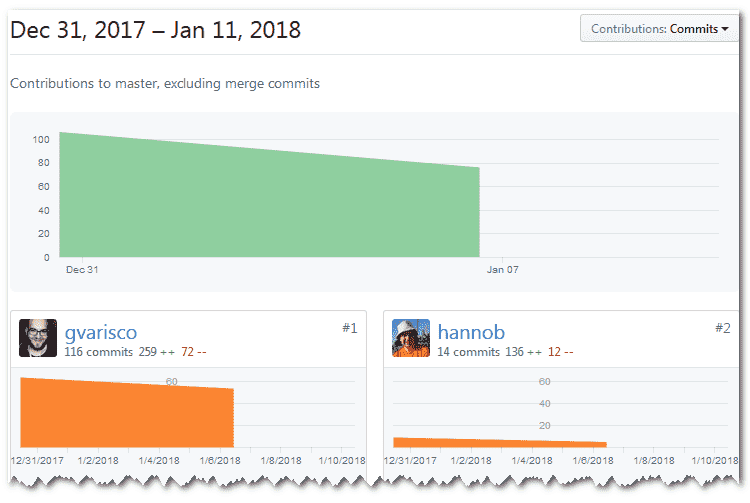
Sounds strange to me, since the very first post of Google project is dated from January 3rd. Not only did they know way before, but also they were prepared since most of the content was posted by everyone at the same time, on the same first day. Sounds like it’s quite organized in the underground cyber-security channels, and for quite a long time too. ????
Another proof that these “threats” are quite well known by a lot of us and that a huge work is going on for quite some time. We got you covered!
The Hasted Released Patches Will Slow You Down 🙂
How will the fixes affect your device? According to the Financial Time, the immediate danger is that the software patches applied to fix the vulnerability will slow down a laptop, server or smartphone. There have already been reports online that suggest a degradation in performance of more than 20 per cent once fixes have been applied. Intel has said that the level of slowdown could be as high as 30 per cent for the most active programs, blah blah bah.
Let’s analyze the “reports” they cite in their “serious” blog:
heads up: Fix for intel hardware bug will lead to performance regressions
This is a single, lone post from some PostgreSQL developer that complains about the upcoming x86 patch series for Linux Kernel 4.16 that will unfortunately cause performance regressions. It’s not even been tested since the kernel has not been released.
Upcoming versions of the linux kernel (and apparently also windows and others), will include new feature that apparently has been implemented with haste to work around an intel hardware bug.
Actually, behind the scenes, this is related to the KAISER patch set, which addresses Kernel leaks known since 2003. It’s been delayed for years because of the CPU overhead associated, but with this regain of attention it’s being pushed forward.
[callout type="default" size="lg"]Originally proposed to protect from side-channel attacks against KASLR, this patch set in-advertently impedes Meltdown as well.
KAISER In brief
KAISER patch set will address Meltdown only.
KAISER patch will mitigate the bug. It’s not a definitive fix.
KAISER will affect performance for anything that does system calls or
interrupts: everything.
Nowhere is the Spectre bug mentioned because this name was invented last year, by Google’s Project Zero team ????
This set of patches will certainly address that. Well, that’s a lot of reports, yeah.
What Are Meltdown and Spectre Actually?
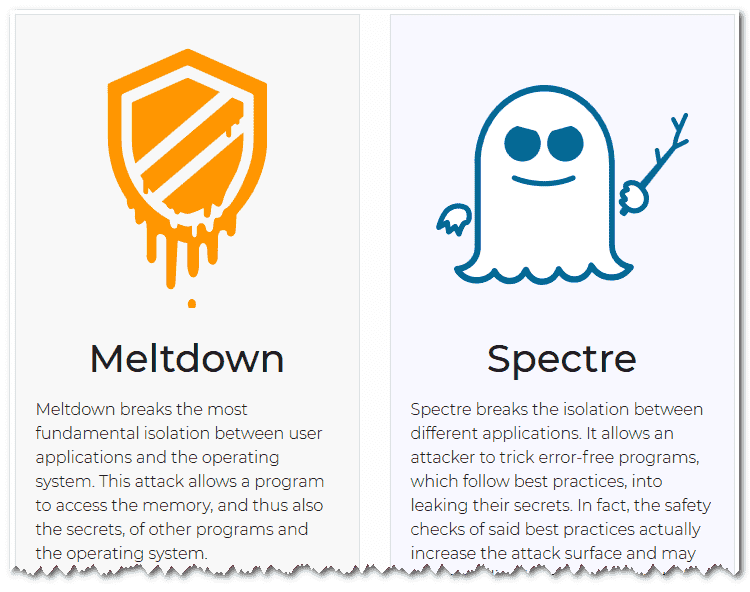
Meltdown and Spectre exploit critical vulnerabilities in modern processors (ntldr: Intel CPUs). These hardware vulnerabilities allow programs to steal data which is currently processed on the computer. While programs are typically not permitted to read data from other programs, a malicious program can exploit Meltdown and Spectre to get hold of secrets stored in the memory of other running programs. This might include your passwords stored in a password manager or browser, your personal photos, emails, instant messages and even business-critical documents.
Pretty scary isn’t it? Doesn’t technically explain anything though. And please notice how they already branded these flaws with CC0 registered logos ????
Now some real information for you:
- Meltdown is a variant of Spectre and aims only Intel chips produced since 1995. Intel claims since January 4th that they are releasing patches for 90% of their late 5 years processors.
- Spectre aims every other, AMD and ARM chips around. The bug is said to be exploitable via JavaScript and WebAssembly. No patches available right now, but it’s very difficult to exploit.
Meltdown vs Spectre
Meltdown vulnerability does not exist on AMD CPUs because they check the security flags upon processes accessing the cache. [/callout]
Can I Test Spectre on my Computer?
Here is a JavaScript code snippet adapted from the Spectre whitepaper example you can paste in your browser’s console (hit F12) to test it against the vulnerability, IF you have an AMD or ARM chip:
var TABLE1_STRIDE = 1;
var TABLE1_BYTES = 3;
var probeTable = ['alpha', 'beta', 'corky'];
var simpleByteArray = [0x00, 0x01, 0x02];
var localJunk;
var index = 0;
if (index < simpleByteArray.length) {
index = simpleByteArray[index | 0];
index = (((index * TABLE1_STRIDE) | 0) & (TABLE1_BYTES - 1)) | 0;
localJunk &= probeTable[index | 0] | 0;
}
console.log(localJunk);
Does it returns anything but 0?
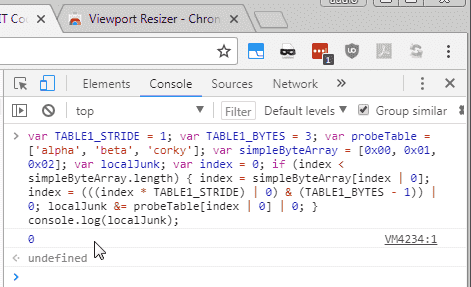
Indeed it doesn’t produce any output on my Core i7 Machine, and anyway this piece of code is totally incomplete to be useful:
It’s missing the entire actual implementation of the Spectre attack, which requires analysis of read times to see if you’re hitting the processor cache or not. The greatest risks are for users of shared computers such as hosted environments that run several different virtual machines on the same hardware.
So, why do experts claim it’s possible to attack with JavaScript? It’s only one part of a complex attack. Again, No need to panic.
Can I Test Meltdown on my Computer?
spectreattack.com links to a Proof of Concept written in C: Github Meltdown PoC. This repository contains several applications, demonstrating the Meltdown bug. You have to compile it for your platform, including dependencies.
So, it’s a code compilation. It needs to be distributed, via compromised libraries, repositories, npm, etc
So, any anti-virus can handle that. End of commotion.
Can I be or Have I been infected?
Till today, January 10th, 2018, Nobody knows.
- cloudlinux.com:
We don’t know just how pervasive the problem is, and how it can be exploited;
We don’t know if the patch accepted by mainline kernel fixes the vulnerability completely;
We don’t know if the patch will crash servers under some workloads;
We don’t know what information about vulnerability becomes public and which details will be revealed.
The described threat has not been seen in the public domain.
Has it been attacked “in the wild”? Nothing has been detected as being exploited in the wild so far. Since these vulnerabilities have been disclosed by security researchers rather than being discovered in an active attack, it’s likely that attackers were not aware of these vulnerabilities until everyone else.
- etc, etc
In short, nobody knows anything about it, and no one ever heard about exploits anywhere.
Even if you didn’t patch your devices, who cares? According to Project Zero team at Google, this exploit is extremely difficult to achieve and relying solely on JavaScript to hack some device is not sufficient. Just try to read the whitepapers and you will understand what I mean.
Although the flaws have existed for 15 years and have been studied seriously since June 2017, there are no signs yet that they have been exploited.
What to Do?
As a cloud hosting using Intel CPUs and Xen PV, you have some patch deployments and reboots under your sleeve.
As an individual, nothing, really.
The research described was performed in a controlled, dedicated lab environment by a highly knowledgeable team with detailed, non-public information until the whitepapers were redacted. It’s rocket science, really. As of today, not even Google researchers could produce a working JavaScript PoC to demonstrate Spectre as a real world application. All this commotion is produced by a highly conceptual and academical work.
To me that’s a good example of how industry can over react against rumors and potential, speculative threats. Remember the 2000 bug hoax. Good money was made back then!
As usual:
- Keep your software up to date
- Accept the patches and releases provided
- Keep you anti-virus up to date
That’s it. We got you covered!