SSL Configuration for Dummies
4 min readDealing with SSL Configuration for Apache or nginx is not easy. There are so many ciphers, and we are constantly reading about breaches and exploits caused by some cipher… If you look around, a lot of bloggers propose this and that snippet of configuration, claiming it’s the best. Thus, after some time searching the web, you will feel like you are completely lost!
Hopefully, Mozilla offer an SSL Configuration Generator, to help you decide between security and availability. It’s AUTO-MAGIC!
Why Does It Matter
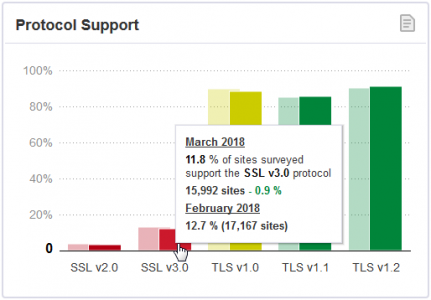
It does matter because lots of highly ranked websites are still using poor SSL Configuration, as reported by the SSL Pulse observatory of Qualys:
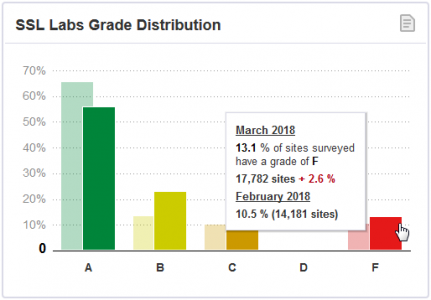
The more the word is spread, the safer the Internet will be!
Mozilla SSL Configuration Generator
It’s so easy to use, I had trouble adding comments!
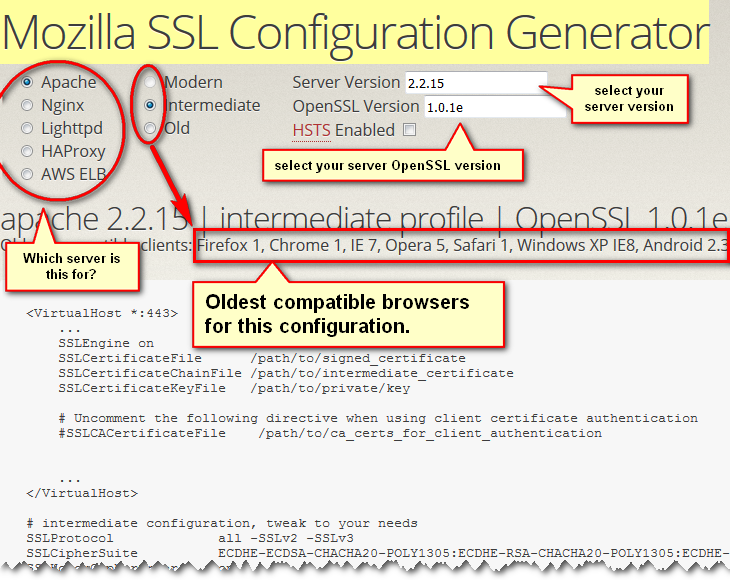
What to know:
This tool is the definitive way to go for generating the SSL Cipher Suite for your needs. It covers the five major brands, that is: Apache, nginx, lighttpd, HAProxy and AWS ELB.
They offer 3 security configuration modes, resulting in a set of ciphers your server will propose to the clients. Be aware that each cipher you disable will render older browser more and more incompatible. It gives you the oldest version of compatible browsers for your convenience.
Example 1: nginx 1.10.3 | old profile | OpenSSL 1.0.1e
The configuration generated renders these browser incompatibles:
- IE 6 XP
- Java 6u45
Mozilla claims they should work, but testssl prove them wrong. Not sure why, but you can run your own tests and as they say, “tweak to your needs!”
This configuration exposes you to these threats:
- Weak 128 Bit ciphers (SEED, IDEA, RC[2,4]): an attacker could brute force the keys used to encrypt the SSL traffic
- SWEET32 (CVE-2016-2183, CVE-2016-6329): VULNERABLE, uses 64 bit block ciphers, because of 3DES
- BEAST (CVE-2011-3389): VULNERABLE, because of SSL3 or TLS1
- LUCKY13 (CVE-2013-0169), experimental potentially VULNERABLE, uses cipher block chaining (CBC) ciphers with TLS. Check patches
Example 2: nginx 1.10.3 | intermediate profile | OpenSSL 1.0.1e
The configuration generated renders these browser incompatibles:
- IE 6 XP
- Java 6u45
This configuration exposes you to these threats:
- SWEET32 (CVE-2016-2183, CVE-2016-6329): VULNERABLE, uses 64 bit block ciphers, because of 3DES
- BEAST (CVE-2011-3389): VULNERABLE, because of SSL3 or TLS1
- LUCKY13 (CVE-2013-0169), experimental potentially VULNERABLE, uses cipher block chaining (CBC) ciphers with TLS. Check patches
Example 3: nginx 1.10.3 | modern profile | OpenSSL 1.0.1e
The configuration generated renders these browser incompatibles:
- Android 2.3.7
- Android 4.1.1
- Android 4.3
- Firefox 26-
- Chrome 29-
- IE 6 XP
- IE 7 Vista
- IE 8 XP
- IE 8 Win 7
- IE 9 Win 7
- IE 10 Win 7
- Safari 5.1.9 OS X 10.6.8
- Safari 8-
- Opera 16-
- Tor 17.0.9 Win 7
- Java 6u45
- Java 7u25
As you can see, this edge configuration that will protect you from SWEET32 (CVE-2016-2183, CVE-2016-6329) and BEAST (CVE-2011-3389) will deny a lot of ancient clients to connect your site.
This configuration exposes you to these threats:
- LUCKY13 (CVE-2013-0169), experimental potentially VULNERABLE, uses cipher block chaining (CBC) ciphers with TLS. Check patches
Note about LUCKY13 vulnerability:
The TLS protocol 1.1 and 1.2 and the DTLS protocol 1.0 and 1.2, as used in OpenSSL, OpenJDK, PolarSSL, and other products, do not properly consider timing side-channel attacks on a MAC check requirement during the processing of malformed CBC padding, which allows remote attackers to conduct distinguishing attacks and plaintext-recovery attacks via statistical analysis of timing data for crafted packets, aka the “Lucky Thirteen” issue.
It’s… not quite clear, is it? That’s because it’s the top level of hacking, and as mentioned by testssl, it’s still experimental since its discovery in 2013. It’s like the Spectre and Meltdown vulnerability: discovered by researchers, being addressed for years, and still not exploited, AFAIK. No need to panic.
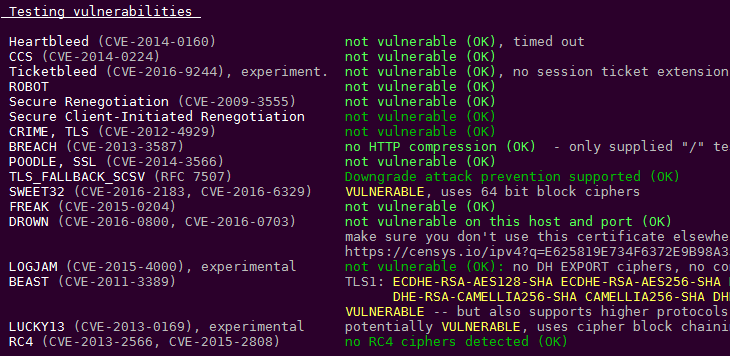
Test Your SSL Configuration With testssl!
This is a bash script that you can download from Github, see more information on how to test your SSL Configuration with testssl.
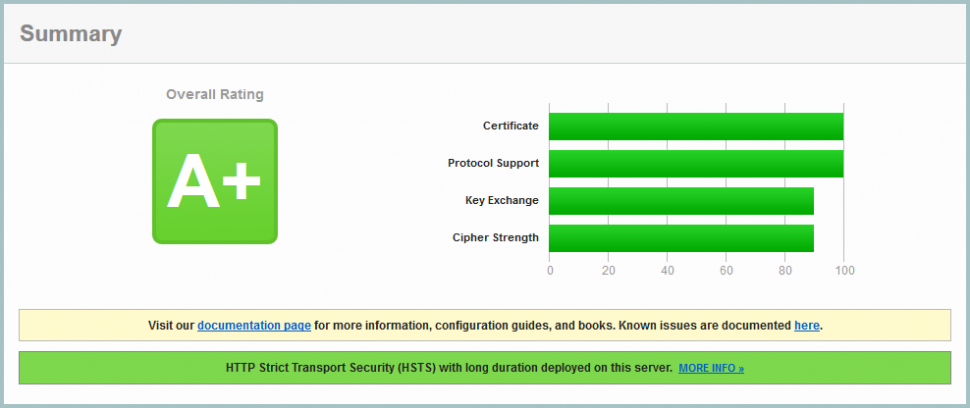
Test Your SSL Configuration With Qualys!
Testing your https site with Qualys SSL Server Test will certainly give you some insights for the next steps:
Final Thoughts
For a public site, a modern configuration with TLS 1.2 only will be fine. For an intranet, beware. Lots of companies still rely on outdated technologies because they use proprietary software based on Java, and the companies providing these solutions are really slow to adopt new standards. I’m not saying Java is the problem, but expensive software solutions are always based on Java.
4 years ago, when I left the Public company I worked for, they were still relying heavily on MSIE 6 XP for their internal back-office transactions. YES you have read correctly, Microsoft Internet Explorer 6.0 on Windows XP. 4 years ago makes it 2014, it was barely yesterday. Your desktop was likely using Windows Seven or 8 at that time. Incredible, isn’t it?
Look at that: 12% of the top 150,000 Alexa ranked websites are still proposing the POODLE attack via SSLv3 SSL Configuration: