WordPress Security 2024: Best Scan Detection Protection
9 min read
wordpress security 2024 scan detection protection featured meme
Web scan detection is a threat to your WordPress security. Scans are performed by malicious actors or bots, looking for open doors, and vulnerabilities in plugins. These scans can be used to identify outdated plugins, themes, or WordPress core versions that have known security vulnerabilities. Once these vulnerabilities are identified, attackers can exploit them to gain unauthorized access to the website, steal sensitive data, or use the website to launch further attacks. WordPress Security 2024: Best Scan Detection Protection against script kiddies and bad bots is here to tell you how to mitigate these risks.
Presentation
What Even is a Scan Detection?
The first step in a targeted attack (of your site) is to identify open doors and forgotten plugins, or known plugin bugs. Malicious actors will regularly scan suspected WordPress sites for flaws and doors left open. How does that look like? Here is an example that happened to me moments ago:
52.169.64.230 - - "GET /wp-content/plugins/core/include.php HTTP/2.0" 403 0 "-" "-" 52.169.64.230 - - "GET /wp-includes/js/tinymce/skins/lightgray/img/ HTTP/2.0" 403 199 "-" "-" 52.169.64.230 - - "GET /wp-mail.php HTTP/2.0" 403 2476 "-" "-" 52.169.64.230 - - "GET /wp-content/themes/twentyfive/include.php HTTP/2.0" 403 0 "-" "-" 52.169.64.230 - - "GET /.well-known/wso112233.php HTTP/2.0" 404 55692 "-" "-" 52.169.64.230 - - "GET /wp-content/shell20211028.php HTTP/2.0" 404 55704 "-" "-" 52.169.64.230 - - "GET /wp-content/themes/travel/issue.php HTTP/2.0" 404 55830 "-" "-" 52.169.64.230 - - "GET /wp-content/themes/travelscape/json.php HTTP/2.0" 404 55850 "-" "-" 52.169.64.230 - - "GET /wp-content/plugins/contact-form-7/includes/js/jquery-ui/themes/smo 52.169.64.230 - - "GET /wp-admin/admin.php HTTP/2.0" 403 2439 "-" "-"
52.169.64.230 - - "GET /assets/css/403.php HTTP/2.0" 301 162 "-" "-" 52.169.64.230 - - "GET /assets/css/403.php HTTP/2.0" 404 55749 "-" "-" 52.169.64.230 - - "GET /403.php HTTP/2.0" 301 162 "-" "-" 52.169.64.230 - - "GET /403.php HTTP/2.0" 404 55619 "-" "-" 52.169.64.230 - - "GET /wp-content/plugins/core/include.php HTTP/2.0" 403 0 "-" "-" 52.169.64.230 - - "GET /wp-includes/js/tinymce/skins/lightgray/img/ HTTP/2.0" 403 199 "-" "-" 52.169.64.230 - - "GET /wp-mail.php HTTP/2.0" 403 2476 "-" "-" 52.169.64.230 - - "GET /wp-content/themes/twentyfive/include.php HTTP/2.0" 403 0 "-" "-"
52.169.64.230 - - "GET /wp-content/plugins/hellopress/wp_filemanager.php HTTP/2.0" 404 55900 "-" "-" 52.169.64.230 - - "GET /wp-includes/Requests/about.php HTTP/2.0" 404 55809 "-" "-" 52.169.64.230 - - "GET /wp-includes/style-engine/about.php HTTP/2.0" 404 55829 "-" "-" 52.169.64.230 - - "GET /radio.php HTTP/2.0" 404 55627 "-" "-" 52.169.64.230 - - "GET /chosen.php HTTP/2.0" 404 55631 "-" "-" 52.169.64.230 - - "GET /simple.php HTTP/2.0" 404 55631 "-" "-" 52.169.64.230 - - "GET /class.api.php HTTP/2.0" 404 55643 "-" "-" 52.169.64.230 - - "GET /wp-head.php HTTP/2.0" 404 55635 "-" "-" 52.169.64.230 - - "GET /file.php HTTP/2.0" 404 55623 "-" "-" 52.169.64.230 - - "GET /assets/css/403.php HTTP/2.0" 404 55749 "-" "-" 52.169.64.230 - - "GET /403.php HTTP/2.0" 404 55619 "-" "-" 52.169.64.230 - - "GET /wp-content/plugins/core/include.php HTTP/2.0" 403 0 "-" "-" 52.169.64.230 - - "GET /.well-known/admin.php HTTP/2.0" 404 55676 "-" "-" 52.169.64.230 - - "GET /mah.php HTTP/2.0" 404 55619 "-" "-" 52.169.64.230 - - "GET /cong.php HTTP/2.0" 404 55623 "-" "-" 52.169.64.230 - - "GET /wp-includes/js/tinymce/skins/lightgray/img/ HTTP/2.0" 403 199 "-" "-" 52.169.64.230 - - "GET /wp-admin/includes/class_api.php HTTP/2.0" 404 55814 "-" "-" 52.169.64.230 - - "GET /wp-mail.php HTTP/2.0" 403 2476 "-" "-" 52.169.64.230 - - "GET /wp-content/themes/twentyfive/include.php HTTP/2.0" 403 0 "-" "-" 52.169.64.230 - - "GET /wp-content/themes/twentyseventeen/page/ HTTP/2.0" 404 55850 "-" "-" 52.169.64.230 - - "GET /.tmb/class_api.php HTTP/2.0" 404 55664 "-" "-" 52.169.64.230 - - "GET /cgi-bin/about.php HTTP/2.0" 403 0 "-" "-" 52.169.64.230 - - "GET /.well-known/acme-challenge/cloud.php HTTP/2.0" 404 55839 "-" "-" 52.169.64.230 - - "GET /repeater.php HTTP/2.0" 404 55639 "-" "-" 52.169.64.230 - - "GET /wp-admin/dropdown.php HTTP/2.0" 404 55676 "-" "-" 52.169.64.230 - - "GET /wp-admin/css/ HTTP/2.0" 403 199 "-" "-" 52.169.64.230 - - "GET /dropdown.php HTTP/2.0" 404 55639 "-" "-" 52.169.64.230 - - "GET /about.php HTTP/2.0" 404 55627 "-" "-" 52.169.64.230 - - "GET /admin.php HTTP/2.0" 404 55627 "-" "-" 52.169.64.230 - - "GET /wp-admin/images/ HTTP/2.0" 403 199 "-" "-" 52.169.64.230 - - "GET /wp-admin/css/colors/ HTTP/2.0" 403 199 "-" "-" 52.169.64.230 - - "GET /wp-content/plugins/seoplugins/mar.php HTTP/2.0" 404 55845 "-" "-" 52.169.64.230 - - "GET /.well-known/pki-validation/xmrlpc.php HTTP/2.0" 404 55844 "-" "-" 52.169.64.230 - - "GET /.well-known/acme-challenge/xmrlpc.php HTTP/2.0" 404 55844 "-" "-" 52.169.64.230 - - "GET /wp-admin/network/xmrlpc.php HTTP/2.0" 404 55794 "-" "-" 52.169.64.230 - - "GET /cgi-bin/xmrlpc.php?p= HTTP/2.0" 403 0 "-" "-" 52.169.64.230 - - "GET /wp-admin/user/xmrlpc.php HTTP/2.0" 404 55779 "-" "-" 52.169.64.230 - - "GET /wp-admin/images/xmrlpc.php HTTP/2.0" 404 55789 "-" "-" 52.169.64.230 - - "GET /ccx/ HTTP/2.0" 404 55603 "-" "-" 52.169.64.230 - - "GET /wp-content/ccx/ HTTP/2.0" 404 55648 "-" "-" 52.169.64.230 - - "GET /wp-admin/ccx/ HTTP/2.0" 404 55640 "-" "-" 52.169.64.230 - - "GET /wp-content/index.php HTTP/2.0" 200 0 "-" "-" 52.169.64.230 - - "GET /wp-info.php HTTP/2.0" 404 55635 "-" "-" 52.169.64.230 - - "GET /wp-blog.php HTTP/2.0" 404 55635 "-" "-" 52.169.64.230 - - "GET /wp-admin/x.php?action=768776e296b6f286f26796e2a72607e2972647 HTTP/2.0" 404 55832 "-" "-" 52.169.64.230 - - "GET /wp-admin/css/colors/blue/about.php HTTP/2.0" 404 55831 "-" "-" 52.169.64.230 - - "GET /cjfuns.php HTTP/2.0" 404 55631 "-" "-" 52.169.64.230 - - "GET /wp-config-sample.php HTTP/2.0" 500 2412 "-" "-" 52.169.64.230 - - "GET /wp-content/plugins/index.php HTTP/2.0" 200 0 "-" "-" 52.169.64.230 - - "GET /worm0.PhP7 HTTP/2.0" 404 55631 "-" "-" 52.169.64.230 - - "GET /wp.php HTTP/2.0" 404 55615 "-" "-" 52.169.64.230 - - "GET /404.php HTTP/2.0" 404 55619 "-" "-" 52.169.64.230 - - "GET /gawean.PhP7 HTTP/2.0" 404 55635 "-" "-" 52.169.64.230 - - "GET /.well-known/acme-challenge/license.php HTTP/2.0" 404 55849 "-" "-" 52.169.64.230 - - "GET /wp-includes/blocks/table/int/tmpl/ HTTP/2.0" 404 55826 "-" "-" 52.169.64.230 - - "GET /wp-admin/css/colors/coffee/ HTTP/2.0" 403 199 "-" "-" 52.169.64.230 - - "GET /wp-includes/themes.php HTTP/2.0" 404 55680 "-" "-" 52.169.64.230 - - "GET /wp-includes/plugins.php HTTP/2.0" 404 55684 "-" "-" 52.169.64.230 - - "GET /wp-content/plugins/revslider/includes/external/page/ HTTP/2.0" 404 55917 "-" "-" 52.169.64.230 - - "GET /users.php HTTP/2.0" 404 55627 "-" "-" 52.169.64.230 - - "GET /wp-admin/js/about.php HTTP/2.0" 404 55764 "-" "-" 52.169.64.230 - - "GET /yanz.php HTTP/2.0" 404 55623 "-" "-" 52.169.64.230 - - "GET /wp-content/plugins/Cache/Cache.php HTTP/2.0" 404 55830 "-" "-" 52.169.64.230 - - "GET /alfanew.php HTTP/2.0" 404 55635 "-" "-" 52.169.64.230 - - "GET /alfa-rex.php7 HTTP/2.0" 404 55643 "-" "-" 52.169.64.230 - - "GET /alfa-rex.php HTTP/2.0" 404 55639 "-" "-" 52.169.64.230 - - "GET /wp-includes/Requests/Text/admin.php HTTP/2.0" 404 55835 "-" "-" 52.169.64.230 - - "GET /images/cloud.php HTTP/2.0" 404 55656 "-" "-" 52.169.64.230 - - "GET /wp-admin/network/cloud.php HTTP/2.0" 404 55789 "-" "-" 52.169.64.230 - - "GET /.well-known/pki-validation/cloud.php HTTP/2.0" 404 55839 "-" "-" 52.169.64.230 - - "GET /wp-admin/images/about.php HTTP/2.0" 404 55784 "-" "-" 52.169.64.230 - - "GET /wp-admin/css/about.php HTTP/2.0" 404 55769 "-" "-" 52.169.64.230 - - "GET /wp-content/gallery/about.php HTTP/2.0" 404 55799 "-" "-" 52.169.64.230 - - "GET /wp-includes/rest-api/about.php HTTP/2.0" 404 55809 "-" "-" 52.169.64.230 - - "GET /wp-includes/SimplePie/about.php HTTP/2.0" 404 55814 "-" "-" 52.169.64.230 - - "GET /wp-content/banners/about.php HTTP/2.0" 404 55799 "-" "-" 52.169.64.230 - - "GET /wp-content/about.php HTTP/2.0" 404 55672 "-" "-" 52.169.64.230 - - "GET /.well-known/about.php HTTP/2.0" 404 55676 "-" "-" 52.169.64.230 - - "GET /wp-includes/Text/about.php HTTP/2.0" 404 55789 "-" "-" 52.169.64.230 - - "GET /wp-includes/ID3/about.php HTTP/2.0" 404 55784 "-" "-" 52.169.64.230 - - "GET /wp-includes/widgets/about.php HTTP/2.0" 404 55804 "-" "-" 52.169.64.230 - - "GET /wp-includes/IXR/about.php HTTP/2.0" 404 55784 "-" "-" 52.169.64.230 - - "GET /.well-known/pki-validation/about.php HTTP/2.0" 404 55839 "-" "-" 52.169.64.230 - - "GET /wp-includes/pomo/about.php HTTP/2.0" 404 55789 "-" "-" 52.169.64.230 - - "GET /wp-includes/block-patterns/about.php HTTP/2.0" 404 55839 "-" "-" 52.169.64.230 - - "GET /wp-content/themes/about.php HTTP/2.0" 404 55794 "-" "-" 52.169.64.230 - - "GET /wp-admin/includes/about.php HTTP/2.0" 404 55794 "-" "-" 52.169.64.230 - - "GET /images/about.php HTTP/2.0" 404 55656 "-" "-" 52.169.64.230 - - "GET /wp-includes/images/about.php HTTP/2.0" 404 55799 "-" "-" 52.169.64.230 - - "GET /wp-includes/about.php HTTP/2.0" 404 55676 "-" "-" 52.169.64.230 - - "GET /nf_tracking.php HTTP/2.0" 404 55651 "-" "-" 52.169.64.230 - - "GET /wp-pano.php HTTP/2.0" 404 55635 "-" "-" 52.169.64.230 - - "GET /defaul1.php HTTP/2.0" 404 55635 "-" "-" 52.169.64.230 - - "GET /wp-content/wso.php HTTP/2.0" 404 55664 "-" "-" 52.169.64.230 - - "GET /themes.php HTTP/2.0" 404 55631 "-" "-" 52.169.64.230 - - "GET /xl2023.php HTTP/2.0" 404 55631 "-" "-" 52.169.64.230 - - "GET /fm1.php HTTP/2.0" 404 55619 "-" "-" 52.169.64.230 - - "GET /wso112233.php HTTP/2.0" 404 55643 "-" "-" 52.169.64.230 - - "GET /shell20211028.php HTTP/2.0" 404 55659 "-" "-" 52.169.64.230 - - "GET /.well-known/wso112233.php HTTP/2.0" 404 55692 "-" "-" 52.169.64.230 - - "GET /wp-content/shell20211028.php HTTP/2.0" 404 55704 "-" "-" 52.169.64.230 - - "GET /wp-content/themes/travel/issue.php HTTP/2.0" 404 55830 "-" "-" 52.169.64.230 - - "GET /wp-content/themes/travelscape/json.php HTTP/2.0" 404 55850 "-" "-" 52.169.64.230 - - "GET /wp-content/plugins/contact-form-7/includes/js/jquery-ui/themes/smoothness/admin.php HTTP/2.0" 404 56074 "-" "-" 52.169.64.230 - - "GET /wp-admin/admin.php HTTP/2.0" 403 2439 "-" "-" 52.169.64.230 - - "GET /wp-2019.php HTTP/2.0" 404 55635 "-" "-" 52.169.64.230 - - "GET /atomlib.php HTTP/2.0" 404 55635 "-" "-" 52.169.64.230 - - "GET /css.php HTTP/2.0" 404 55619 "-" "-" 52.169.64.230 - - "GET /log.php HTTP/2.0" 404 55619 "-" "-" 52.169.64.230 - - "GET /mail.php HTTP/2.0" 404 55623 "-" "-" 52.169.64.230 - - "GET /lufix.php HTTP/2.0" 404 55627 "-" "-" 52.169.64.230 - - "GET /doc.php HTTP/2.0" 404 55619 "-" "-" 52.169.64.230 - - "GET /bak.php HTTP/2.0" 404 55619 "-" "-" 52.169.64.230 - - "GET /content.php HTTP/2.0" 404 55635 "-" "-" 52.169.64.230 - - "GET /upfile.php HTTP/2.0" 404 55631 "-" "-" 52.169.64.230 - - "GET /wp-conflg.php HTTP/2.0" 404 55643 "-" "-" 52.169.64.230 - - "GET /bypass.php HTTP/2.0" 404 55631 "-" "-" 52.169.64.230 - - "GET /wp-activate.php HTTP/2.0" 302 0 "-" "-"
What Is Being Scanned Here?
Randomly, here is what one can tell by the look of the files targeted:
- http 403 Forbidden
- /wp-admin/admin.php
- /wp-mail.php
- /wp-admin/css/colors/coffee/
- …
- This is the meat of the scan: now they know I have WordPress… Otherwise they would get an http 404 Not Found
- Reason for 403: scanner was not logged in, did not initiate a cookie session, and also because I hide those folders with htaccess
- Low risk, but those 403 identify your site as being WordPress
- http 404 Not Found
- /wp-content/plugins/contact-form-7/includes/js/jquery-ui/themes/smoothness/admin.php
- /wp-content/themes/twentyfive/include.php
- /wp-content/themes/travel/issue.php
- /wp-content/themes/travelscape/json.php
- /wp-content/plugins/core/include.php
- …
- These could be themes with known bugs or exploits
- High risk if you have those plugins
HTTP 404 vs 403: What Can You Do About it?
- http 404: perfect, you want that.
- http 403: you are exposed, since you deny access
Using Nginx
Trivial: create a 403 catch that redirects to a 404 page, inside your server { }
## http 403 catch and throw 404, in case you don;t have AIO WP Security plugin
error_page 403 /404.html;
location = /404.html {
add_header Cache-Control "no-cache" always;
internal; # return 404
# root /var/www/default/error; # or.. return an existing 404 page
# default_type "text/plain; charset=utf-8"; # or.. return a cutom message
# return 404 "$status $status_text\n";
}
Using Apache
Not possible with Apache. All you can do is display a fake 404 error page, but users will recieve a 403.
Using Nginx + WordPress + All In One WP Security
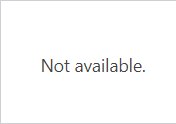
By default, AOI WP Security will catch 403 and display “Not Available” + a WP error:
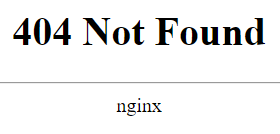
This action happens before the 404 is issued by nginx and instead, you get the bare-bone nginx 404 error:
Not very glamour… Can you do better? Yessir! Add this PHP snippet to fix AIO WP Security and hangle error 404 properly, so your visitors have the usual WP 404 error page:
//Fix to prevent fatal error caused by some themes and Yoast SEO
//do_action('aiowps_before_wp_die_renamed_login');
add_action('aiowps_before_wp_die_renamed_login', 'show_404_page_instead_notavailable');
function show_404_page_instead_notavailable(){
global $wp_query;
status_header(404);
$wp_query->set_404();
if ((($template = get_404_template()) || ($template = get_index_template())) && ($template = apply_filters('template_include', $template))) {
include($template);
}
die;
}
And voila… A real, actual 404 error instead of 403:
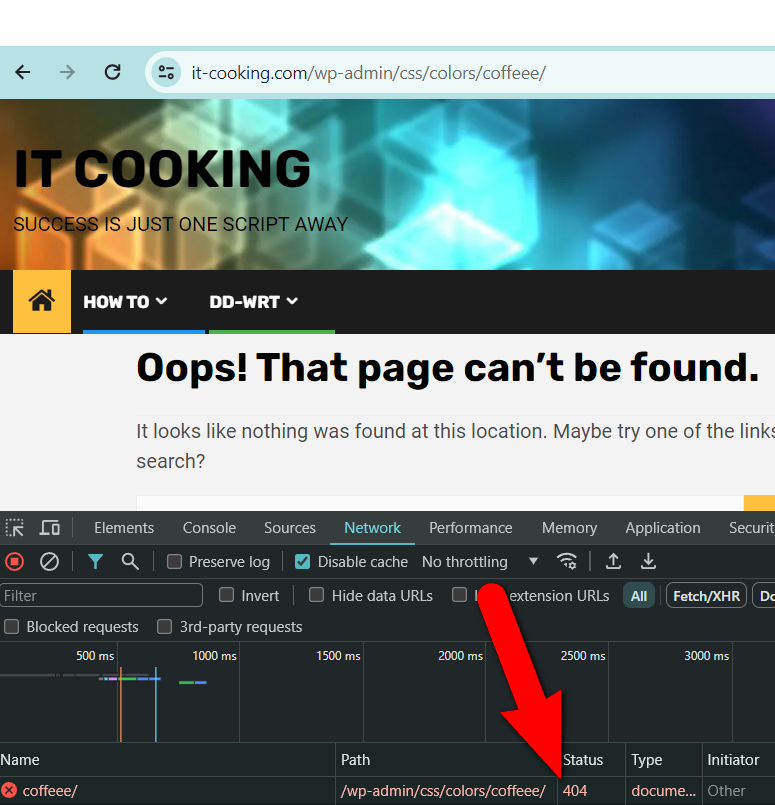 Wrapping Up
Wrapping Up
With all the surveillance and censorship in place everywhere, how do malicious actors still exist in 2024? Well, it’s pretty simple to run bad bots from a free Cloud server or infected computers, and scan a bunch of IP across the board. You can get access to many free server online, courtesy of Cloud providers. If you get kicked out for violation of the TOS, you just open another account elsewhere. And eventually you gain access to someone’s assets, and start the real work from there.
You cannot prevent this from happening, nor can you hide WordPress with 100% accuracy. Plugins like WP Hide & Security Enhancer will go further, by renaming conventional assets such as all the /wp-*/ links, but at the end of the day, your WordPress site still look like WordPress. No matter how much efforts you put in disguising it, there is a look and feel that even you can tell. Especially in the html code generated. However, you can prevent them from detecting too much, and limit your exposure to script kiddies entirely with this technique.