Pi-hole a Network-wide DNS Ad-Blocker aka A black hole for Internet advertisements. Primarily developed for Raspberry Pi and ported to Linux, it’s lightweight. Just like pixelserv (man-in-the-middle https DNS Ad-Blocker), it is also a DNS server.
Read more: How To Install Pi-Hole DNS Ad blocker1. Install a supported operating system
You can run Pi-hole in a container, or deploy it directly to a supported operating system via their automated installer.
Pi-hole Supported Linux distros:
| Distribution | Release | Architecture |
|---|---|---|
| Raspbian | Stretch / Buster | ARM |
| Ubuntu | 16.x / 18.x | ARM / x86_64 |
| Debian | 9 / 10 | ARM / x86_64 / i386 |
| Fedora | 28 / 29 | ARM / x86_64 |
| CentOS | 7 | x86_64 |
If you happen to have another DNS server running such as BIND, you will need to turn it off in order for Pi-hole to respond to DNS queries.
Ubuntu users: This is compatible with systemd-resolve (on AWS, it’s listening on 127.0.0.53 so it does not interfere with Pi-Hole).
2. Install Pi-hole
Their automated installer asks you a few questions and then sets everything up for you. Once complete, move onto step 3.
One-step install:
curl -sSL https://install.pi-hole.net | bash
The installer is interactive.
- DNS: choose Cloudflare (fastest) or Quad9 (Secure)
- Privacy Mode for FTL: Using privacy levels you can specify which level of detail you want to see in your Pi-hole statistics. This question happens only when you choose to install the web admin interface.
Auto-Update and Cron jobs
Cron jobs are created by the installer:
cat /etc/cron.d/pihole # Pi-hole: A black hole for Internet advertisements # (c) 2017 Pi-hole, LLC (https://pi-hole.net) # Network-wide ad blocking via your own hardware. # # Updates ad sources every week # # This file is copyright under the latest version of the EUPL. # Please see LICENSE file for your rights under this license. # # # # This file is under source-control of the Pi-hole installation and update # scripts, any changes made to this file will be overwritten when the softare # is updated or re-installed. Please make any changes to the appropriate crontab # or other cron file snippets. # Pi-hole: Update the ad sources once a week on Sunday at a random time in the # early morning. Download any updates from the adlists # Squash output to log, then splat the log to stdout on error to allow for # standard crontab job error handling. 51 3 * * 7 root PATH="$PATH:/usr/local/bin/" pihole updateGravity >/var/log/pihole_updateGravity.log || cat /var/log/pihole_updateGravity.log # Pi-hole: Flush the log daily at 00:00 # The flush script will use logrotate if available # parameter "once": logrotate only once (default is twice) # parameter "quiet": don't print messages 00 00 * * * root PATH="$PATH:/usr/local/bin/" pihole flush once quiet @reboot root /usr/sbin/logrotate /etc/pihole/logrotate # Pi-hole: Grab local version and branch every 10 minutes */10 * * * * root PATH="$PATH:/usr/local/bin/" pihole updatechecker local # Pi-hole: Grab remote version every 24 hours 9 16 * * * root PATH="$PATH:/usr/local/bin/" pihole updatechecker remote @reboot root PATH="$PATH:/usr/local/bin/" pihole updatechecker remote reboot
3. Status Check
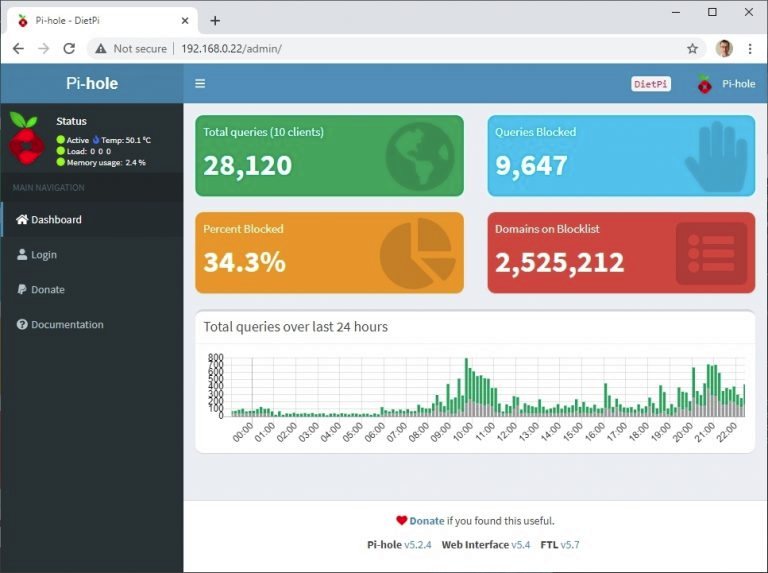
Web UI: Change your password!
pihole -a -p
Web UI Configuration
The web UI showcase logs and point & click configuration. If you chose to install lighttpd, the web UI is available at your pihole IP/admin
To use your existing web server, create a virtual host which points to /var/www/html where Pi-Hole installed its web UI.
Command Line
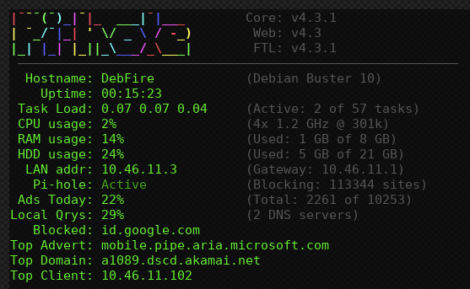
You don’t need to install the Web UI to check Pi-hole status. Especially on Raspberry Pi for which this Ad-blocker has been designed, a simple command line dashboard is available to check the server status:
pihole -c
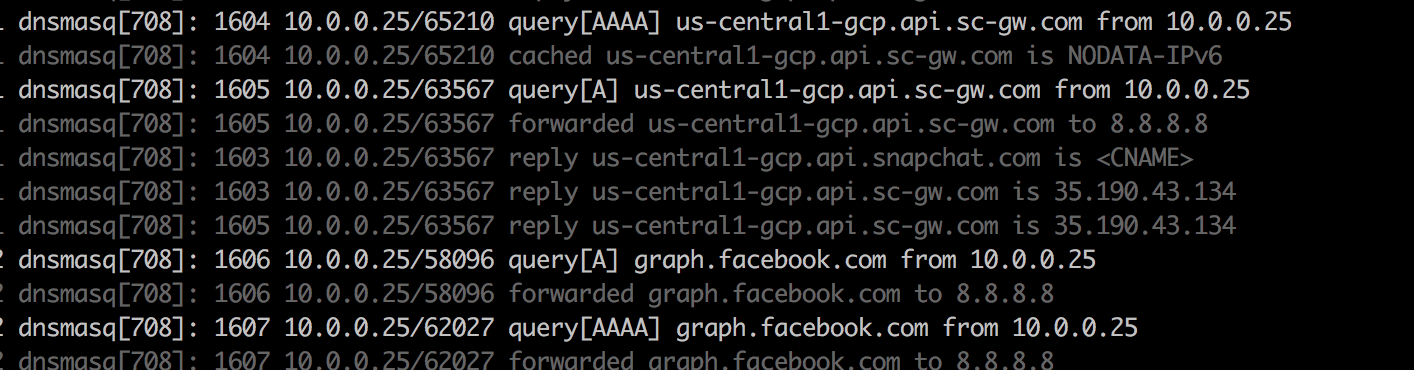
You can also follow the DNS logs directly:
pihole -t
4. Use Pi-hole as your DNS server
Depending on what and where you installed Pi-Hole, consider modifying your devices accordingly.
If your Pi-Hole is installed on a public IP server, consider updating your ISP or DD-wrt router to use that DNS as well! You can also share it with your friends! also consider installing it both online and at home, for redundancy.
Example 1 Home router
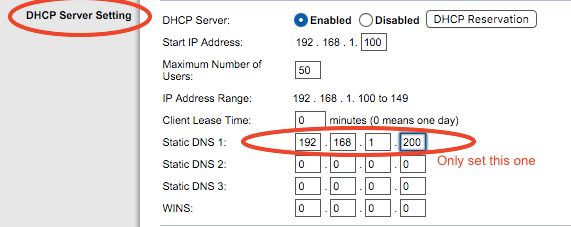
Modify the home or ISP router to use that DNS instead of the default. All your home connected devices will be protected!
Some crappy routers will force you to define two different DNS addresses. Use 127.0.0.1 as secondary DNS or install another Pi-hole server online or at home. The secondary DNS is naver used unless the first one is down.
Example 2 Individual Protection
You can also setup each device individually. This guide will show you how to do it on most platforms including Android, Apple Mac and iPhone.
For instance on Windows, open Adapter Options:
You can also access Adapter Options by running this command:
::{26EE0668-A00A-44D7-9371-BEB064C98683}\3\::{7007ACC7-3202-11D1-AAD2-00805FC1270E}
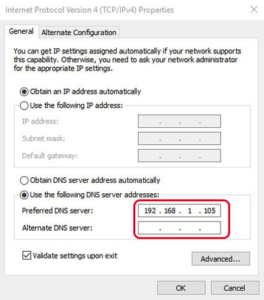
Right-click on your network card and setup the IPv4 DNS manually.
Example 3 Pi-Hole with VPN Server
This is the recommended setup. Not only your ISP cannot track you anymore, but you also utterly destroy any attempt from Ad servers to bug you anymore, transparently and setup-free!
If you are running an OpenVPN server for instance (How To Install OpenVPN Server here), you need to define the new Pi-Hole DNS address in the /etc/openvpn/server.conf file.
To do so, save, then edit the config file, and keep only one line if you have only one Pi-Hole DNS address (replace 1.2.3.4 by your Pi-Hole DNS IP):
vi /etc/openvpn/server.conf push "dhcp-option DNS 1.2.3.4"
Then restart the OpenVPN service:
service openvpn restart
Pi-Hole used as the main DNS of the OpenVPN server will effectively filter Ads for any client using that VPN. Also setup the home ISP router and your secondary DD-wrt router to use it so even your home devices are protected!
5. Enjoy
I disabled browser Ad-blocker plugins such as uBlock Origin and started surfing over the Ad-bloated Macworld.com and other fake news mainstream medias. I also noticed some Ads on iPhone games were absent but not all of them.
Test Pi-hole Ad-blocking Power
Do you see any ads? If you see Ads, maybe that’s because they are hosted (same url as the main website) aka interstitial Ads. Pi-hole can do nothing for self-hosted Ads and you need to pair it with browser Ad-Blockers like uBlock Origin.
The best of all? Most of the mobile Ads on Apple and Android phones are blocked as well! No more stupid Ad countdown interrupting my son’s games!
Not all of them will be blocked because, again, some are still self-hosted on the game developer’s platform.