How To Test SSL Configurations With testssl.sh
4 min read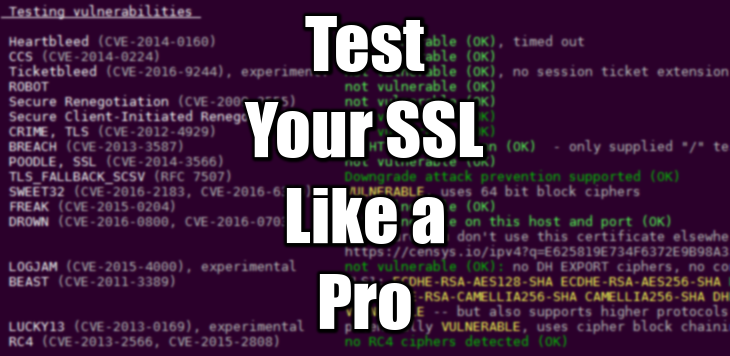
Is your current SSL Configuration secure enough? Is you https site rejecting old clients? Here comes a great tool called testssl.sh. It’s a bash script, developed by drwetter on Github, to test SSL Configurations
Enabling SSL for your site is a great idea overall. However, navigate around the multitude of SSL Configurations available for Apache and nginx is quite daunting. What’s best? What’s most secure? Are you privileging compatibility against security? testssl will help you decide what’s best for your site.
Pre-Requisite: OpenSSL
I will assume that you already have an up-to-date, secure OpenSSL version. If unsure, upgrade OpenSSL first (Debian/Ubuntu command):
sudo apt-get install --only-upgrade openssl
# openssl is already the newest version (1.1.0g-2.1+ubuntu16.04.1+deb.sury.org+1).
For an overview of how to generate SSL Configuration for Apache and nginx automatically, check this post on Mozilla SSL Configuration Generator.
Last minute discovery
Since version 2.9, testssl is packaged with static OpenSSL binaries used for the tests. Therefore, your system OpenSSL version has no connection whatsoever with the test results. Having an up-to-date version it is still important though.
Install testssl on Debian/Ubuntu 12-17
testssl comes packaged with Debian. However the last stable version for your release may not be be up-to-date. Bellow is the proof that you should NOT install testssl.sh with your packager:
sudo apt-get -y install testssl.sh
testssl yourdomain.com
###########################################################
testssl 2.6 from https://testssl.sh/
(1.379B 2015/09/25 12:35:41)
This program is free software. Distribution and
modification under GPLv2 permitted.
USAGE w/o ANY WARRANTY. USE IT AT YOUR OWN RISK!
Please file bugs @ https://testssl.sh/bugs/
###########################################################
Using “OpenSSL 1.1.0g 2 Nov 2017” [~143 ciphers] on
web-scav-01:/usr/bin/openssl
(built: “reproducible build, date unspecified”, platform: “debian-amd64”)
Testing now (2018-03-06 16:11) —> real.ip.address:443 (yourdomain.com) <—
rDNS (real.ip.address): your-iaas-provider.domain.com.
Service detected: HTTP
–> Testing protocols (via sockets except TLS 1.2 and SPDY/NPN)
SSLv2 not offered (OK)
SSLv3 not offered (OK)
TLS 1 offered
TLS 1.1 offered
TLS 1.2 offered (OK)
SPDY/NPN Local problem: /usr/bin/openssl doesn’t support SPDY/NPN
–> Testing ~standard cipher lists
Null Ciphers not offered (OK)
Anonymous NULL Ciphers not offered (OK)
Anonymous DH Ciphers not offered (OK)
40 Bit encryption Local problem: No 40 Bit encryption configured in /usr/bin/openssl
56 Bit encryption Local problem: No 56 Bit encryption configured in /usr/bin/openssl
Export Ciphers (general) Local problem: No Export Ciphers (general) configured in /usr/bin/openssl
Low (<=64 Bit) Local problem: No Low (<=64 Bit) configured in /usr/bin/openssl
DES Ciphers Local problem: No DES Ciphers configured in /usr/bin/openssl
Medium grade encryption not offered (OK)
Triple DES Ciphers Local problem: No Triple DES Ciphers configured in /usr/bin/openssl
High grade encryption offered (OK)
–> Testing (perfect) forward secrecy, (P)FS — omitting 3DES, RC4 and Null Encryption here
PFS is offered (OK) ECDHE-RSA-AES256-GCM-SHA384 DHE-RSA-AES256-GCM-SHA384 DHE-RSA-AES256-SHA256 DHE-RSA-AES256-SHA ECDHE-RSA-AES256-SHA384 ECDHE-RSA-AES256-SHA ECDHE-RSA-AES128-GCM-SHA256 ECDHE-RSA-AES128-SHA256 DHE-RSA-AES128-GCM-SHA256 DHE-RSA-AES128-SHA256 DHE-RSA-AES128-SHA ECDHE-RSA-AES128-SHA
–> Testing server preferences
Has server cipher order? yes (OK)
Negotiated protocol TLSv1.2
Negotiated cipher ECDHE-RSA-AES128-GCM-SHA256, 256 bit ECDH
Cipher order
TLSv1: ECDHE-RSA-AES128-SHA ECDHE-RSA-AES256-SHA DHE-RSA-AES128-SHA DHE-RSA-AES256-SHA AES128-SHA AES256-SHA
TLSv1.1: ECDHE-RSA-AES128-SHA ECDHE-RSA-AES256-SHA DHE-RSA-AES128-SHA DHE-RSA-AES256-SHA AES128-SHA AES256-SHA
TLSv1.2: ECDHE-RSA-AES128-GCM-SHA256 ECDHE-RSA-AES256-GCM-SHA384 DHE-RSA-AES128-GCM-SHA256 DHE-RSA-AES256-GCM-SHA384 ECDHE-RSA-AES128-SHA256 ECDHE-RSA-AES256-SHA384 ECDHE-RSA-AES128-SHA ECDHE-RSA-AES256-SHA DHE-RSA-AES128-SHA256 DHE-RSA-AES128-SHA DHE-RSA-AES256-SHA256 DHE-RSA-AES256-SHA AES128-GCM-SHA256 AES256-GCM-SHA384 AES128-SHA256 AES256-SHA256 AES128-SHA AES256-SHA
Local problem: /usr/bin/openssl doesn’t support SPDY/NPN
–> Testing server defaults (Server Hello)
TLS server extensions server name, renegotiation info, EC point formats, status request
Session Tickets RFC 5077 (none)
Server key size 2048 bit
Signature Algorithm SHA256 with RSA
Fingerprint / Serial SHA1 437F1FA12994BD3CAC6FF721707AC0D8B256C321 / 03FBB1AEEAC5BF0118F06B6EB1B4AF90DD19
SHA256 E625819E734F6372E9B98A35946A7A5E923130C63D586D319F23B0EEB0E744C0
Common Name (CN) subject=CN = yourdomain.com (CN in response to request w/o SNI: subject=CN = yourdomain.com)
subjectAltName (SAN) admin.yourdomain.com blog.yourdomain.com cdn.yourdomain.com yourdomain.com www.admin.yourdomain.com www.blog.yourdomain.com www.cdn.yourdomain.com www.yourdomain.com
Issuer issuer=C = US, O = Let’s Encrypt, CN = Let’s Encrypt Authority X3 (issuer=C = US, O = Let’s Encrypt, CN = Let’s Encrypt Authority X3)
EV cert (experimental) no
Certificate Expiration >= 60 days (2018-02-13 16:26 –> 2018-05-14 17:26 -0400)
# of certificates provided 2
Certificate Revocation List
OCSP URI http://ocsp.int-x3.letsencrypt.org
OCSP stapling offered
TLS timestamp random values, no fingerprinting possible
–> Testing HTTP header response @ “/”
HTTP Status Code 301 Moved Permanently, redirecting to “https://www.yourdomain.com/”
HTTP clock skew 0 sec from localtime
Strict Transport Security —
Public Key Pinning —
Server banner nginx/1.10.3 (Ubuntu)
Application banner —
Cookie(s) (none issued at “/”)
Security headers —
Reverse Proxy banner —
–> Testing vulnerabilities
Heartbleed (CVE-2014-0160) not vulnerable (OK) (timed out)
CCS (CVE-2014-0224) not vulnerable (OK)
Secure Renegotiation (CVE-2009-3555) not vulnerable (OK)
Secure Client-Initiated Renegotiation not vulnerable (OK)
CRIME, TLS (CVE-2012-4929) Local problem: /usr/bin/openssl lacks zlib support
BREACH (CVE-2013-3587) no HTTP compression (OK) (only “/” tested)
POODLE, SSL (CVE-2014-3566) not vulnerable (OK)
TLS_FALLBACK_SCSV (RFC 7507), experim. Local problem: /usr/bin/openssl lacks TLS_FALLBACK_SCSV support
FREAK (CVE-2015-0204) Local problem: /usr/bin/openssl doesn’t have any EXPORT RSA ciphers configured
LOGJAM (CVE-2015-4000), experimental Local problem: /usr/bin/openssl doesn’t have any DHE EXPORT ciphers configured
BEAST (CVE-2011-3389) no CBC ciphers for TLS1 (OK)
RC4 (CVE-2013-2566, CVE-2015-2808) no RC4 ciphers detected (OK)
–> Testing all locally available 143 ciphers against the server, ordered by encryption strength
Hexcode Cipher Suite Name (OpenSSL) KeyExch. Encryption Bits
————————————————————————-
xc030 ECDHE-RSA-AES256-GCM-SHA384 ECDH 256 AESGCM 256
x9f DHE-RSA-AES256-GCM-SHA384 DH 2048 AESGCM 256
xc028 ECDHE-RSA-AES256-SHA384 ECDH 256 AES 256
x6b DHE-RSA-AES256-SHA256 DH 2048 AES 256
xc014 ECDHE-RSA-AES256-SHA ECDH 256 AES 256
x39 DHE-RSA-AES256-SHA DH 2048 AES 256
x9d AES256-GCM-SHA384 RSA AESGCM 256
x3d AES256-SHA256 RSA AES 256
x35 AES256-SHA RSA AES 256
xc02f ECDHE-RSA-AES128-GCM-SHA256 ECDH 256 AESGCM 128
x9e DHE-RSA-AES128-GCM-SHA256 DH 2048 AESGCM 128
xc027 ECDHE-RSA-AES128-SHA256 ECDH 256 AES 128
x67 DHE-RSA-AES128-SHA256 DH 2048 AES 128
xc013 ECDHE-RSA-AES128-SHA ECDH 256 AES 128
x33 DHE-RSA-AES128-SHA DH 2048 AES 128
x9c AES128-GCM-SHA256 RSA AESGCM 128
x3c AES128-SHA256 RSA AES 128
x2f AES128-SHA RSA AES 128
Done now (2018-03-06 16:11) —> real.ip.address:443 (yourdomain.com) <—
[/code]sudo apt-get -y purge testssl.sh
Warnings you will get
40 Bit encryption Local problem: No 40 Bit encryption configured in /usr/bin/openssl 56 Bit encryption Local problem: No 56 Bit encryption configured in /usr/bin/openssl Export Ciphers (general) Local problem: No Export Ciphers (general) configured in /usr/bin/openssl Low (<=64 Bit) Local problem: No Low (<=64 Bit) configured in /usr/bin/openssl DES Ciphers Local problem: No DES Ciphers configured in /usr/bin/openssl Triple DES Ciphers Local problem: No Triple DES Ciphers configured in /usr/bin/openssl Local problem: /usr/bin/openssl doesn't support SPDY/NPN
This means the version of testssl you are using is out-of-date, or incompatible with the OpenSSL version installed. See the next section to know why, and the section after to install the latest dev release.
Packaged Versions of testssl are Out-of-date
Let’s see which version of testssl you get for which OS:
- ubuntu 12.04 – 16.04 LTS: testssl.sh_2.6
- ubuntu 17.10 LTS: testssl.sh_2.8~rc3
- ubuntu 18.04 LTS: testssl.sh_2.9.5-1
So this is why. Unless you upgrade your server to the latest release, you won’t get the latest testssl version.
Download the Latest testssl.sh Release
Install and Test
You will need Github to do that, because from version 2.9, testssl comes packaged with some /etc files. You cannot just download and launch the script by itself anymore. This recipe will help you install it on the local user folders under /usr/local/src/.
The following analysis has been done for a site using an intermediate SSL Configuration (TLSv1 + TLSv1.1 + TLSv1.2) generated by Mozilla SSL Configuration Generator. See how it works here: SSL Configuration for Dummies.
# uninstall the package first: sudo apt-get -y purge testssl.sh git clone --depth 1 https://github.com/drwetter/testssl.sh.git /usr/local/src/testssl.sh ln -s /usr/local/src/testssl.sh/testssl.sh /usr/local/bin/testssl
testssl yourdomain.com
###########################################################
testssl 2.9dev from https://testssl.sh/dev/
This program is free software. Distribution and
modification under GPLv2 permitted.
USAGE w/o ANY WARRANTY. USE IT AT YOUR OWN RISK!
Please file bugs @ https://testssl.sh/bugs/
###########################################################
Using “OpenSSL 1.0.2-chacha (1.0.2i-dev)” [~183 ciphers]
on web-scav-01:/usr/local/src/testssl.sh/bin/openssl.Linux.x86_64
(built: “Jun 22 19:32:29 2016”, platform: “linux-x86_64”)
Start 2018-03-07 16:46:13 –>> real.ip.address:443 (yourdomain.com) <<–
rDNS (real.ip.address): your-iaas-provider.domain.com.
Service detected: HTTP
Testing protocols via sockets except NPN+ALPN
SSLv2 not offered (OK)
SSLv3 not offered (OK)
TLS 1 offered
TLS 1.1 offered
TLS 1.2 offered (OK)
TLS 1.3 not offered
NPN/SPDY h2, http/1.1 (advertised)
ALPN/HTTP2 h2, http/1.1 (offered)
Testing cipher categories
NULL ciphers (no encryption) not offered (OK)
Anonymous NULL Ciphers (no authentication) not offered (OK)
Export ciphers (w/o ADH+NULL) not offered (OK)
LOW: 64 Bit + DES encryption (w/o export) not offered (OK)
Weak 128 Bit ciphers (SEED, IDEA, RC[2,4]) not offered (OK)
Triple DES Ciphers (Medium) offered
High encryption (AES+Camellia, no AEAD) offered (OK)
Strong encryption (AEAD ciphers) offered (OK)
Testing robust (perfect) forward secrecy, (P)FS — omitting Null Authentication/Encryption, 3DES, RC4
PFS is offered (OK) ECDHE-RSA-AES256-GCM-SHA384 ECDHE-RSA-AES256-SHA384 ECDHE-RSA-AES256-SHA DHE-RSA-AES256-GCM-SHA384 DHE-RSA-AES256-SHA256 DHE-RSA-AES256-SHA ECDHE-RSA-AES128-GCM-SHA256
ECDHE-RSA-AES128-SHA256 ECDHE-RSA-AES128-SHA DHE-RSA-AES128-GCM-SHA256 DHE-RSA-AES128-SHA256 DHE-RSA-AES128-SHA
Elliptic curves offered: prime256v1
Testing server preferences
Has server cipher order? yes (OK)
Negotiated protocol TLSv1.2
Negotiated cipher ECDHE-RSA-AES128-GCM-SHA256, 256 bit ECDH (P-256)
Cipher order
TLSv1: ECDHE-RSA-AES128-SHA ECDHE-RSA-AES256-SHA DHE-RSA-AES128-SHA DHE-RSA-AES256-SHA ECDHE-RSA-DES-CBC3-SHA EDH-RSA-DES-CBC3-SHA AES128-SHA AES256-SHA DES-CBC3-SHA
TLSv1.1: ECDHE-RSA-AES128-SHA ECDHE-RSA-AES256-SHA DHE-RSA-AES128-SHA DHE-RSA-AES256-SHA ECDHE-RSA-DES-CBC3-SHA EDH-RSA-DES-CBC3-SHA AES128-SHA AES256-SHA DES-CBC3-SHA
TLSv1.2: ECDHE-RSA-AES128-GCM-SHA256 ECDHE-RSA-AES256-GCM-SHA384 DHE-RSA-AES128-GCM-SHA256 DHE-RSA-AES256-GCM-SHA384 ECDHE-RSA-AES128-SHA256 ECDHE-RSA-AES256-SHA384 ECDHE-RSA-AES128-SHA ECDHE-RSA-AES256-SHA
DHE-RSA-AES128-SHA256 DHE-RSA-AES128-SHA DHE-RSA-AES256-SHA256 DHE-RSA-AES256-SHA ECDHE-RSA-DES-CBC3-SHA EDH-RSA-DES-CBC3-SHA AES128-GCM-SHA256 AES256-GCM-SHA384 AES128-SHA256 AES256-SHA256 AES128-SHA
AES256-SHA DES-CBC3-SHA
Testing server defaults (Server Hello)
TLS extensions (standard) “server name/#0” “renegotiation info/#65281” “EC point formats/#11” “status request/#5” “heartbeat/#15” “next protocol/#13172” “application layer protocol negotiation/#16”
Session Ticket RFC 5077 hint (no lifetime advertised)
SSL Session ID support yes
Session Resumption Tickets: yes, ID: yes
TLS clock skew Random values, no fingerprinting possible
Signature Algorithm SHA256 with RSA
Server key size RSA 2048 bits
Server key usage Digital Signature, Key Encipherment
Server extended key usage TLS Web Server Authentication, TLS Web Client Authentication
Serial / Fingerprints 03FBB1AEEAC5BF0118F06B6EB1B4AF90DD19 / SHA1 437F1FA12994BD3CAC6FF721707AC0D8B256C321
SHA256 E625819E734F6372E9B98A35946A7A5E923130C63D586D319F23B0EEB0E744C0
Common Name (CN) yourdomain.com
subjectAltName (SAN) admin.yourdomain.com blog.yourdomain.com cdn.yourdomain.com yourdomain.com www.admin.yourdomain.com www.blog.yourdomain.com www.cdn.yourdomain.com www.yourdomain.com
Issuer Let’s Encrypt Authority X3 (Let’s Encrypt from US)
Trust (hostname) Ok via SAN and CN (same w/o SNI)
Chain of trust Ok
EV cert (experimental) no
Certificate Validity (UTC) 67 >= 30 days (2018-02-13 16:26 –> 2018-05-14 17:26)
# of certificates provided 2
Certificate Revocation List —
OCSP URI http://ocsp.int-x3.letsencrypt.org
OCSP stapling offered
OCSP must staple extension —
DNS CAA RR (experimental) not offered
Certificate Transparency —
Testing HTTP header response @ “/”
HTTP Status Code 301 Moved Permanently, redirecting to “https://www.yourdomain.com/”
HTTP clock skew 0 sec from localtime
Strict Transport Security —
Public Key Pinning —
Server banner nginx/1.10.3 (Ubuntu)
Application banner —
Cookie(s) (none issued at “/”) — maybe better try target URL of 30x
Security headers —
Reverse Proxy banner —
Testing vulnerabilities
Heartbleed (CVE-2014-0160) not vulnerable (OK), timed out
CCS (CVE-2014-0224) not vulnerable (OK)
Ticketbleed (CVE-2016-9244), experiment. not vulnerable (OK), no session ticket extension
ROBOT not vulnerable (OK)
Secure Renegotiation (CVE-2009-3555) not vulnerable (OK)
Secure Client-Initiated Renegotiation not vulnerable (OK)
CRIME, TLS (CVE-2012-4929) not vulnerable (OK)
BREACH (CVE-2013-3587) no HTTP compression (OK) – only supplied “/” tested
POODLE, SSL (CVE-2014-3566) not vulnerable (OK)
TLS_FALLBACK_SCSV (RFC 7507) Downgrade attack prevention supported (OK)
SWEET32 (CVE-2016-2183, CVE-2016-6329) VULNERABLE, uses 64 bit block ciphers
FREAK (CVE-2015-0204) not vulnerable (OK)
DROWN (CVE-2016-0800, CVE-2016-0703) not vulnerable on this host and port (OK)
make sure you don’t use this certificate elsewhere with SSLv2 enabled services
https://censys.io/ipv4?q=E625819E734F6372E9B98A35946A7A5E923130C63D586D319F23B0EEB0E744C0 could help you to find out
LOGJAM (CVE-2015-4000), experimental not vulnerable (OK): no DH EXPORT ciphers, no common primes detected
BEAST (CVE-2011-3389) TLS1: ECDHE-RSA-AES128-SHA ECDHE-RSA-AES256-SHA DHE-RSA-AES128-SHA DHE-RSA-AES256-SHA ECDHE-RSA-DES-CBC3-SHA EDH-RSA-DES-CBC3-SHA AES128-SHA AES256-SHA DES-CBC3-SHA
VULNERABLE — but also supports higher protocols TLSv1.1 TLSv1.2 (likely mitigated)
LUCKY13 (CVE-2013-0169), experimental potentially VULNERABLE, uses cipher block chaining (CBC) ciphers with TLS. Check patches
RC4 (CVE-2013-2566, CVE-2015-2808) no RC4 ciphers detected (OK)
Testing 364 ciphers via OpenSSL plus sockets against the server, ordered by encryption strength
Hexcode Cipher Suite Name (OpenSSL) KeyExch. Encryption Bits Cipher Suite Name (RFC)
—————————————————————————————————————————–
xc030 ECDHE-RSA-AES256-GCM-SHA384 ECDH 256 AESGCM 256 TLS_ECDHE_RSA_WITH_AES_256_GCM_SHA384
xc028 ECDHE-RSA-AES256-SHA384 ECDH 256 AES 256 TLS_ECDHE_RSA_WITH_AES_256_CBC_SHA384
xc014 ECDHE-RSA-AES256-SHA ECDH 256 AES 256 TLS_ECDHE_RSA_WITH_AES_256_CBC_SHA
x9f DHE-RSA-AES256-GCM-SHA384 DH 2048 AESGCM 256 TLS_DHE_RSA_WITH_AES_256_GCM_SHA384
x6b DHE-RSA-AES256-SHA256 DH 2048 AES 256 TLS_DHE_RSA_WITH_AES_256_CBC_SHA256
x39 DHE-RSA-AES256-SHA DH 2048 AES 256 TLS_DHE_RSA_WITH_AES_256_CBC_SHA
x9d AES256-GCM-SHA384 RSA AESGCM 256 TLS_RSA_WITH_AES_256_GCM_SHA384
x3d AES256-SHA256 RSA AES 256 TLS_RSA_WITH_AES_256_CBC_SHA256
x35 AES256-SHA RSA AES 256 TLS_RSA_WITH_AES_256_CBC_SHA
xc02f ECDHE-RSA-AES128-GCM-SHA256 ECDH 256 AESGCM 128 TLS_ECDHE_RSA_WITH_AES_128_GCM_SHA256
xc027 ECDHE-RSA-AES128-SHA256 ECDH 256 AES 128 TLS_ECDHE_RSA_WITH_AES_128_CBC_SHA256
xc013 ECDHE-RSA-AES128-SHA ECDH 256 AES 128 TLS_ECDHE_RSA_WITH_AES_128_CBC_SHA
x9e DHE-RSA-AES128-GCM-SHA256 DH 2048 AESGCM 128 TLS_DHE_RSA_WITH_AES_128_GCM_SHA256
x67 DHE-RSA-AES128-SHA256 DH 2048 AES 128 TLS_DHE_RSA_WITH_AES_128_CBC_SHA256
x33 DHE-RSA-AES128-SHA DH 2048 AES 128 TLS_DHE_RSA_WITH_AES_128_CBC_SHA
x9c AES128-GCM-SHA256 RSA AESGCM 128 TLS_RSA_WITH_AES_128_GCM_SHA256
x3c AES128-SHA256 RSA AES 128 TLS_RSA_WITH_AES_128_CBC_SHA256
x2f AES128-SHA RSA AES 128 TLS_RSA_WITH_AES_128_CBC_SHA
xc012 ECDHE-RSA-DES-CBC3-SHA ECDH 256 3DES 168 TLS_ECDHE_RSA_WITH_3DES_EDE_CBC_SHA
x16 EDH-RSA-DES-CBC3-SHA DH 2048 3DES 168 TLS_DHE_RSA_WITH_3DES_EDE_CBC_SHA
x0a DES-CBC3-SHA RSA 3DES 168 TLS_RSA_WITH_3DES_EDE_CBC_SHA
Running client simulations via sockets
Android 2.3.7 TLSv1.0 DHE-RSA-AES128-SHA, 2048 bit DH
Android 4.1.1 TLSv1.0 ECDHE-RSA-AES128-SHA, 256 bit ECDH (P-256)
Android 4.3 TLSv1.0 ECDHE-RSA-AES128-SHA, 256 bit ECDH (P-256)
Android 4.4.2 TLSv1.2 ECDHE-RSA-AES128-GCM-SHA256, 256 bit ECDH (P-256)
Android 5.0.0 TLSv1.2 ECDHE-RSA-AES128-GCM-SHA256, 256 bit ECDH (P-256)
Android 6.0 TLSv1.2 ECDHE-RSA-AES128-GCM-SHA256, 256 bit ECDH (P-256)
Android 7.0 TLSv1.2 ECDHE-RSA-AES128-GCM-SHA256, 256 bit ECDH (P-256)
Chrome 51 Win 7 TLSv1.2 ECDHE-RSA-AES128-GCM-SHA256, 256 bit ECDH (P-256)
Chrome 57 Win 7 TLSv1.2 ECDHE-RSA-AES128-GCM-SHA256, 256 bit ECDH (P-256)
Firefox 49 Win 7 TLSv1.2 ECDHE-RSA-AES128-GCM-SHA256, 256 bit ECDH (P-256)
Firefox 53 Win 7 TLSv1.2 ECDHE-RSA-AES128-GCM-SHA256, 256 bit ECDH (P-256)
IE 6 XP No connection
IE 7 Vista TLSv1.0 ECDHE-RSA-AES128-SHA, 256 bit ECDH (P-256)
IE 8 XP TLSv1.0 DES-CBC3-SHA
IE 8 Win 7 TLSv1.0 ECDHE-RSA-AES128-SHA, 256 bit ECDH (P-256)
IE 11 Win 7 TLSv1.2 DHE-RSA-AES128-GCM-SHA256, 2048 bit DH
IE 11 Win 8.1 TLSv1.2 DHE-RSA-AES128-GCM-SHA256, 2048 bit DH
IE 11 Win Phone 8.1 Update TLSv1.2 DHE-RSA-AES128-GCM-SHA256, 2048 bit DH
IE 11 Win 10 TLSv1.2 ECDHE-RSA-AES128-GCM-SHA256, 256 bit ECDH (P-256)
Edge 13 Win 10 TLSv1.2 ECDHE-RSA-AES128-GCM-SHA256, 256 bit ECDH (P-256)
Edge 13 Win Phone 10 TLSv1.2 ECDHE-RSA-AES128-GCM-SHA256, 256 bit ECDH (P-256)
Opera 17 Win 7 TLSv1.2 ECDHE-RSA-AES128-SHA256, 256 bit ECDH (P-256)
Safari 5.1.9 OS X 10.6.8 TLSv1.0 ECDHE-RSA-AES128-SHA, 256 bit ECDH (P-256)
Safari 7 iOS 7.1 TLSv1.2 ECDHE-RSA-AES128-SHA256, 256 bit ECDH (P-256)
Safari 9 OS X 10.11 TLSv1.2 ECDHE-RSA-AES128-GCM-SHA256, 256 bit ECDH (P-256)
Safari 10 OS X 10.12 TLSv1.2 ECDHE-RSA-AES128-GCM-SHA256, 256 bit ECDH (P-256)
Apple ATS 9 iOS 9 TLSv1.2 ECDHE-RSA-AES128-GCM-SHA256, 256 bit ECDH (P-256)
Tor 17.0.9 Win 7 TLSv1.0 ECDHE-RSA-AES128-SHA, 256 bit ECDH (P-256)
Java 6u45 No connection
Java 7u25 TLSv1.0 ECDHE-RSA-AES128-SHA, 256 bit ECDH (P-256)
Java 8u31 TLSv1.2 ECDHE-RSA-AES128-GCM-SHA256, 256 bit ECDH (P-256)
OpenSSL 1.0.1l TLSv1.2 ECDHE-RSA-AES128-GCM-SHA256, 256 bit ECDH (P-256)
OpenSSL 1.0.2e TLSv1.2 ECDHE-RSA-AES128-GCM-SHA256, 256 bit ECDH (P-256)
Done 2018-03-07 16:47:17 [ 66s] –>> real.ip.address:443 (yourdomain.com) <<–
[/code]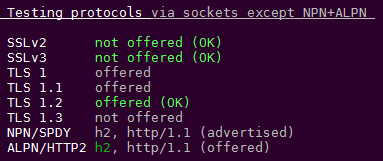
No warnings anymore: much better isn’t it?
Verify Who Can Still Connect to Your Site
It’s worth noting that this marvelous tool will give you a list of client browsers that can still connect to your site with your current state-of-the-art configuration. Because as stated in the presentation, the more secure you go, the less old browsers will be able to connect.
Report from testssl
For the test above, for instance, most clients are compatible with your cipher-suite. testssl will report some old clients won’t be able to open your site:
_Running client simulations via sockets_ ... Android 7.0 TLSv1.2 ECDHE-RSA-AES256-GCM-SHA384, 256 bit ECDH (P-256) Chrome 57 Win 7 TLSv1.2 ECDHE-RSA-AES256-GCM-SHA384, 256 bit ECDH (P-256) Firefox 53 Win 7 TLSv1.2 ECDHE-RSA-AES256-GCM-SHA384, 256 bit ECDH (P-256) IE 11 Win 10 TLSv1.2 ECDHE-RSA-AES256-GCM-SHA384, 256 bit ECDH (P-256) IE 6 XP No connection Java 6u45 No connection ...
Report from Qualys
Testing your https site with Qualys SSL Server Test will give you a much more detailed list of clients compatibles with your configuration.
# Not simulated clients (Protocol mismatch):
| Android 2.3.7 No SNI 2 | Protocol mismatch (not simulated) | ||
| Android 4.0.4 | Protocol mismatch (not simulated) | ||
| Android 4.1.1 | Protocol mismatch (not simulated) | ||
| Android 4.2.2 | Protocol mismatch (not simulated) | ||
| Android 4.3 | Protocol mismatch (not simulated) | ||
| Baidu Jan 2015 | Protocol mismatch (not simulated) | ||
| IE 6 / XP No FS 1 No SNI 2 | Protocol mismatch (not simulated) | ||
| IE 7 / Vista | Protocol mismatch (not simulated) | ||
| IE 8 / XP No FS 1 No SNI 2 | Protocol mismatch (not simulated) | ||
| IE 8-10 / Win 7 R | Protocol mismatch (not simulated) | ||
| IE 10 / Win Phone 8.0 | Protocol mismatch (not simulated) | ||
| Java 6u45 No SNI 2 | Protocol mismatch (not simulated) | ||
| Java 7u25 | Protocol mismatch (not simulated) | ||
| OpenSSL 0.9.8y | Protocol mismatch (not simulated) | ||
| Safari 5.1.9 / OS X 10.6.8 | Protocol mismatch (not simulated) | ||
| Safari 6.0.4 / OS X 10.8.4 R | Protocol mismatch (not simulated) | ||
| (1) Clients that do not support Forward Secrecy (FS) are excluded when determining support for it. | |||
| (2) No support for virtual SSL hosting (SNI). Connects to the default site if the server uses SNI. | |||
| (3) Only first connection attempt simulated. Browsers sometimes retry with a lower protocol version. | |||
| (R) Denotes a reference browser or client, with which we expect better effective security. | |||
| (All) We use defaults, but some platforms do not use their best protocols and features (e.g., Java 6 & 7, older IE). | |||
| (All) Certificate trust is not checked in handshake simulation, we only perform TLS handshake. | |||